Maybe this one change in macOS Sierra slipped by until you needed it most. Or maybe you didn’t discovered this little shift until you tried to install a favorite app that you didn’t download from the mac app store. Whatever the manner, you learn the hard way that macOS Sierra’s made invisible the usual method to open apps downloaded from anywhere!
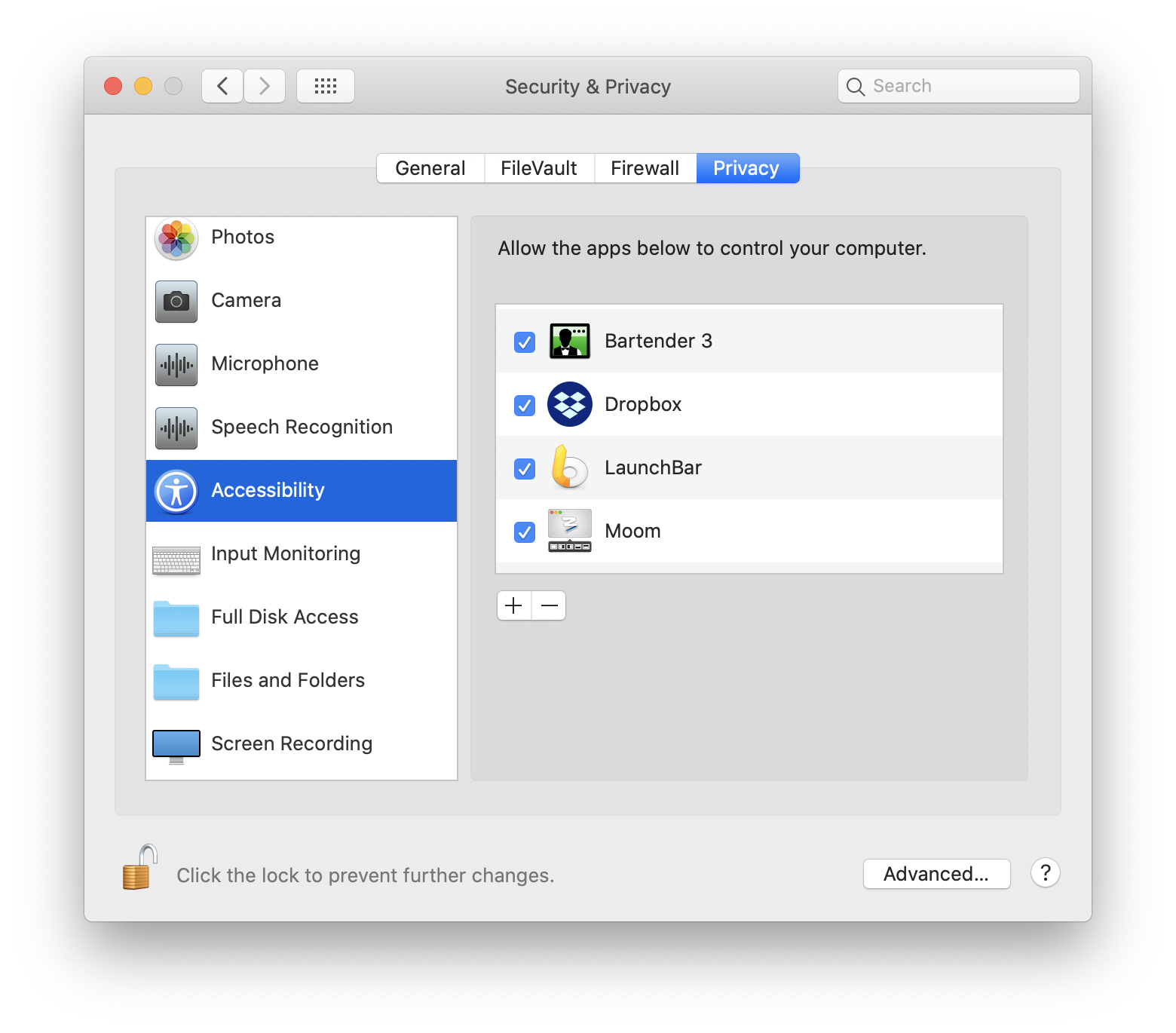
In the 'General' tab, you'll see a section called 'Allow apps downloaded from.' In order to change these settings, you'll have to click on the lock icon below and input your admin password. Once that's out of the way, you can choose between three options: Mac App Store. Mac App Store and identified developers. MacFUSE allows you to extend macOS's native file handling capabilities via third-party file systems. As a user, installing the macFUSE software package will let you use any third-party FUSE file system. Legacy MacFUSE file systems are supported through the optional MacFUSE compatibility layer. As a result, while you could theoretically have tried to make a living writing Lisa software, it was essentially impossible to publish third party GUI apps for the Lisa Office System like the word processor and the spreadsheet app. Eventually the LisaOS became a dev environment for the Macintosh, but not a dev environment for the Lisa itself.
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it. Oct 14, 2017 This tends to happen with every major system software release, either due to compatibility issues, third party apps, bugs, or a variety of other reasons. This article attempts to gather a list of some of the reported macOS High Sierra problems, along with possible troubleshooting solutions to those issues, though by no means is this exhaustive. The 10 must-have utilities for macOS Sierra. You have a slightly ridiculous number of drop-down and status menus in your system menubar from Apple and third-party apps and system components.
The settings was until recently found in the General tab of the Security & Privacy System Preference. But no more, not with macOS. So if you really need that app and can’t figure out how to get it open, it’s frustrating. No, it’s very frustrating that our macs just aren’t working the way the used to!
Since OSX Lion, Apple’s mac operating system includes a security tool named Gatekeeper. This feature prevents downloads of software and apps from unidentified developers. Gatekeeper assumes the app is trouble when the app you want to download is not signed with Apple. And it does not allow that app onto your mac computer. For most mac users, this is a very good thing and helps keep their computers safe and secure. But their are a lot of us iFolk who absolutely need and want the ability to download AND open apps downloaded from anywhere.
Contents
- 1 So What is this Gatekeeper Anyway?
- 3 How-To Open apps Not Available in the app Store
- 4 Terminal Is At Your Command to Open apps Downloaded from Anywhere
- 5 A Word For the Wise
So What is this Gatekeeper Anyway?
In theory, Gatekeeper protects your mac from apps that potentially have adverse affects. It works by not allowing unsigned apps from downloading and opening on your mac. Apple prefers that all 3rd party apps go through its signing process. Developers register with Apple and a unique Developer ID identifies each developer. This ID is then used in testing and validating the app for Apple products. Apple reviews, approves, and accepts all signed apps. Once accepted, the app then officially supports Gatekeeper. And users are able to download and open these apps via the mac app store.
Apple views this method as the safest and most reliable to download new apps onto your mac computers. They believe that downloading apps exclusively from the mac app store translates into reduced hazard. And since Apple’s reviewed the app, if there’s ever a problem, Apple quickly removes it from the mac app store.
Consequently, if an app is developed by an unknown developer with no Developer ID, Gatekeeper blocks that app from being installed and opened. However, there are a lot of great apps out there, particularly open source apps, that for numerous reasons are not available via the mac app store. Many of these third-party apps are thoroughly tested and have worked on macs and other computers for ages. Either by choice or chance, these apps are not currently available in the mac app store.
What About the mac app store?
It’s easy to think that the mac app store works exactly like the app store for iPhones and other iDevices. But not so! Since the mac app store opened, mac computers have always allowed you to install applications not available in the store. Before there was a mac app store (2011), installing applications via third-party websites or installation discs was the norm. Plus, developers must pay a percentage to Apple when you purchase apps from the mac app store. When purchased directly through the developer, there is no additional fees for Apple, keeping costs lower for all of us users. So for these reasons and more, many apps are not included in the mac app store.
Mac users continue (and will continue) to get apps directly from developers sites or old-school via installation discs. The long and short is that the mac app store is not the only way to get apps. So getting around this macOS default is pretty important!
Where is Setting to Open Apps Downloaded from Anywhere?
In previous versions of its mac operating system, there was a checkbox option in System Preferences>Security & Privacy allowing you to download apps from anywhere. However, macOS Sierra introduced a Gatekeeper that’s a heck of a lot more strict than in the past. In this newest os incarnation, Gatekeeper defaults to only allowing options for apps downloaded from the app store or the app store and identified developers. So for us iFolk that want or need to download an app from a source we trust but Apple currently does not trust (or identify), what to do?
We need that third option, the option to “allow apps downloaded from anywhere” that seemingly disappeared with our update to macOS Sierra.
Luckily, there are a couple of ways to circumvent Gatekeeper’s defaults so when we want or need to, we can indeed open apps downloaded from anywhere.
So let’s get to it!

How-To Open apps Not Available in the app Store
The Super Easy Way to Bypass Apple Defaults and Open apps Downloaded from Anywhere
So if your trust the app and its unidentified developer, then there is a really easy way to open that app.
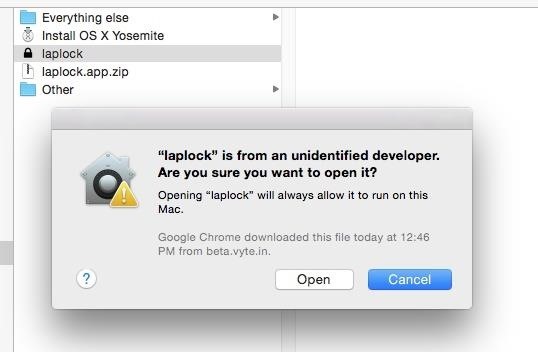
And it’s surprising how simple this method is and basically involves a single click. To selectively bypass Gatekeeper, just Control Click (or Right Click) and choose Open from the menu options. A message appears warning you that the app is from an unidentified developer and asks if you are sure you want to open it? If you are confident in the app’s source, click Open. That’s it!
This option works for single apps. It does update your computer’s internal list of identified developers so in the future, macOS recognizes the developer as “identified.” But this method does not make universal updates to your Security & Privacy System options. It’s a one and done option, for times when you want or need to download and open a particular app that is currently NOT available in the app store. (i.e. the app is not signed.)
Another, Slightly Longer Way to Open apps Downloaded from Anywhere
Assuming you trust the app, after downloading move it to your Applications folder. Now, try to open it. You likely see a warning that the app “can’t be opened because it is from an unidentified developer.” Select OK. But this does not actually open the app.
Now, go to System Preferences>Security & Privacy and select the General tab. Look at the section “Allow apps downloaded from:” and see if the app you just attempted to open is listed with a button “Open Anyway.” If so, click this button to open that app. Be aware that the “Open Anyway” button is only available for around 1 hour after you first try to open the app.
macOS takes note of that app and developer and add it to the operating system’s list of identified developers (for this mac only.) If you ever download another app from this same developer, macOS checks this internal list. If the developer is listed, macOS open any app from that developer.
About the Unidentified Warning Message
When you open an app that is not registered with Apple by an identified developer, you see a warning message box. Seeing this message does not mean there’s something wrong with that particular app. Developers wrote many of these unidentified apps before developer ID registration began. And others choose not to register for various reasons from cost (Apple charges a yearly developer fee) to conviction.
The unidentified developer warning means that the app you want to open has not been reviewed by Apple. Consequently, macOS is not able to check and verify if that app has been modified or broken since it was released.
Once you open an unidentified app, that app is saved as an exception to your security settings. From now on, you open it by double-clicking as normal.
Terminal Is At Your Command to Open apps Downloaded from Anywhere
Use Terminal to update our Security & Privacy options to include the checkbox allowing us to open apps downloaded from anywhere. And it’s actually pretty simple to make this modification.
Although simple, for the average mac user this step is not recommended . Before you download and open an app that Apple does not currently recognize or identify, make sure you (or your company) fully trust the app’s source and its validity. Modifying this security setting puts your computer at potential risk and makes your mac more vulnerable to some malware and other malicious junkware. So, proceed with caution and double (or triple) check the trust factor of any app before downloading and opening.
Allow and Open apps Downloaded from Anywhere
- Quit System Preferences and all open applications
- Open Terminal
- Located in /Applications/Utilities/ folder
- Type in sudo spctl –master-disable
- Press Return
- Type your admin password to confirm
- Open System Preferences>Security & Privacy
- Select General Tab
- Verfiy that “Allow apps downloaded from:” now shows “Anywhere” as an option
Third Parties In The United States
Now, you are able to install and open apps downloaded from anywhere under macOS Sierra. Using this command turns Gatekeeper off and allows apps from anywhere including unidentified developers. Apple issues warnings that these unidentified developer (unsigned) apps possibly make your mac more vulnerable to malware and junkware.
Reverse to Original macOS App Settings
To go back to the macOS default settings, repeat the steps above substituting step 3 with enableinstead of disable at the end of the command.
So step 3 reads like this:
sudo spctl –master-enable
This returns macOS Gatekeeper back to its strict default and disallows unsigned apps from downloading and opening.
Checking the status of Gatekeeper
To check the status of Gatekeeper on your mac without opening System Preferences, it’s as simple as one command. Open Terminal and type the following command: spctl –status. Then press the return key. And you get a response of either “assessments enabled,” meaning Gatekeeper is ON and ACTIVE. Or you see “disabled,” meaning Gatekeeper is OFF and INACTIVE.
A Word For the Wise
When you receive the message “app can’t be opened because it is from an unidentified developer,” take a close look at that app and ensure that you trust its source before downloading and opening. This warning is there to protect your computer and you from harm and malware, so don’t just simply ignore it. Be mindful and careful when downloading apps not currently offered on the mac app store.
With that said, there are a host of wonderful third party apps that are not currently offered in the mac app store. Many of these apps are under review and not yet accepted. Still others do not seek approval based on conviction and values. So don’t discount a good app just because it’s not offered in the mac app store. Do your research and check out an app’s source before deciding to download or not. Think of great apps like NeoOffice that for the longest time wasn’t available on the mac app store but now is!
For most of her professional life, Amanda Elizabeth (Liz for short) trained all sorts of folks on how to use media as a tool to tell their own unique stories. She knows a thing or two about teaching others and creating how-to guides!
Her clients include Edutopia, Scribe Video Center, Third Path Institute, Bracket, The Philadelphia Museum of Art, and the Big Picture Alliance.
Elizabeth received her Master of Fine Arts degree in media making from Temple University, where she also taught undergrads as an adjunct faculty member in their department of Film and Media Arts.
Related Posts:
Third-party apps and extensions expand your editing options in Photos for iOS and macOS. You can apply edits from multiple apps and extensions to one photo, or use any combination of apps and extensions plus the editing tools built into Photos.
Use third-party extensions on your iPhone, iPad, or iPod touch
Learn how to find apps with Photos extensions for your iOS device, turn on the extensions, and then use them to edit photos.
Install iOS apps that offer extensions
Download Macos Sierra On Windows
Use the App Store on your device to find and install apps that allow full editing from Photos or include extensions for Photos. Apps that include Photos extensions often say so in their descriptions; search for terms like 'Photos extension' to explore more apps.
You can also choose from the apps listed in Edit Images Faster With Photo Extensions on the App Store.
Turn on extensions on your iOS device
Third Party List
After you install apps that include Photos extensions on your iPhone, iPad, or iPod touch, turn the extensions on:
- Open the Photos app, then tap a photo.
- Tap Edit, and then tap .
- In the menu that appears, swipe to the left until you see the More button, and then tap it.
- You see your apps that include Photos extensions. You can turn them on or off, or drag them up or down to change their order. When you’re finished, tap Done.
Edit photos with extensions on your iOS device
- Open the Photos app, then tap a photo.
- Tap Edit, then tap .
- Select an app from the menu that appears.
- Edit the photo with the extension's tools.
- When you're satisfied with your edits, click Done. You can choose another extension to apply more edits to the photo, or use any of the editing tools that are built into Photos.
- If you're finished with all edits, click Done to exit the edit mode.
Use third-party extensions on your Mac
Learn how to find apps with Photos extensions for your Mac, turn on the extensions, and then use them to edit photos.
Install Mac apps that allow editing or offer extensions
Photos for macOS makes finding third-party apps easy:
- Double-click a photo in your library to open it in single view, then click Edit.
- Click , then choose App Store.
Macos Sierra App Store
The Mac App Store opens to a selection of third-party photo editing apps that are compatible with Photos.
You can also choose from the apps listed in Extensions for Fast Photo Edits on the App Store.
Turn on extensions on your Mac
After you install apps that include Photos extensions on your Mac, turn the extensions on:
- Choose Apple () menu > System Preferences, then click Extensions.
- Click Photos Editing in the left sidebar. Your apps that include Photos extensions appear.
- Turn on the extensions that you want to use in Photos. You can also drag them up or down to adjust the order that they appear in Photos.
Edit photos with extensions on your Mac
- Double-click a photo in your library to open it in single view, then click Edit.
- Click .
- Choose an app from the menu that appears.
- Edit the photo with the extension's tools that appear.
- When you're satisfied with your edits, click Save Changes. You can choose another extension to apply more edits to the photo, or use any of the editing tools that are built into Photos.
- If you're finished with all edits, click Done to exit the edit mode.
Edit photos within third-party apps on your Mac
With Photos for macOS High Sierra and later, you can send a photo to most third-party photo apps for editing, then save the changes right back into your library.
- Control-click a photo and choose Edit With from the contextual menu. Then choose from the list of third-party editing apps on your Mac. You can also click a photo and then choose Image > Edit With in the menu bar.
- The photo opens in the third-party app that you chose. Make your edits, and then save.
If the app saves photos in a non-standard format, look for an option to save as JPEG or another format that Photos supports.
Your edited photo appears automatically in Photos.
Learn more
- When you edit a photo with third-party extensions or the built-in tools that Photos offers, you can always start over with the original photo. Open the photo in edit mode, then click Revert to Original on your Mac or tap Revert if you're using an iOS device.
- If you use iCloud Photos, remember that it keeps your photos organized and up to date everywhere that you use the same Apple ID. So any edits that you make on one device appear on your other devices too.
This blog post covers several enhancements to Intelligent Tracking Prevention (ITP) in iOS and iPadOS 13.4 and Safari 13.1 on macOS to address our latest discoveries in the industry around tracking.
Full Third-Party Cookie Blocking
Cookies for cross-site resources are now blocked by default across the board. This is a significant improvement for privacy since it removes any sense of exceptions or “a little bit of cross-site tracking is allowed.”
It might seem like a bigger change than it is. But we’ve added so many restrictions to ITP since its initial release in 2017 that we are now at a place where most third-party cookies are already blocked in Safari. To keep supporting cross-site integration, we shipped the Storage Access API two years ago to provide the means for authenticated embeds to get cookie access with mandatory user control. It is going through the standards process in the W3C Privacy Community Group right now.
Regardless of the size of this change, there are further benefits, as explored below.
Paves the Way For Other Browsers
Safari continues to pave the way for privacy on the web, this time as the first mainstream browser to fully block third-party cookies by default. As far as we know, only the Tor Browser has featured full third-party cookie blocking by default before Safari, but Brave just has a few exceptions left in its blocking so in practice they are in the same good place. We know Chrome wants this behavior too and they announced that they’ll be shipping it by 2022.
We will report on our experiences of full third-party cookie blocking to the privacy groups in W3C to help other browsers take the leap.
Removes Statefulness From Cookie Blocking
Full third-party cookie blocking removes statefulness in cookie blocking. As discussed in our December 2019 blog post, the internal state of tracking prevention could be turned into a tracking vector. Full third-party cookie blocking makes sure there’s no ITP state that can be detected through cookie blocking behavior. We’d like to again thank Google for initiating this analysis through their report.
Disables Login Fingerprinting
As discussed by Jeremiah Grossman back in 2008 and Tom Anthony in 2012, and set up by Robin Linus in 2016 as a live demo with which you can test your browser, this technique allows a website to invisibly detect where you are logged in and is viable in any browser without full third-party cookie blocking.
Since “global browser state” has been top of mind in the web privacy community as of late, we’d like to point out that cookies themselves are global state and unless the browser blocks or partitions them in third-party contexts, they allow for cross-site leakage of user information such as login fingerprinting.
Additional Benefits
In addition, there are further benefits to full third-party cookie blocking:
- Disables cross-site request forgery attacks against websites through third-party requests. Note that you still need to protect against forged requests that come in through top frame navigations (see SameSite cookies for guidance).
- Removes the ability to use an auxiliary third-party domain to identify users. Such a setup could otherwise persist IDs even when users delete website data for the first party.
- Simplifies things for developers. Now it’s as easy as possible: If you need cookie access as third-party, use the Storage Access API.
What About the Classifier?
ITP’s classifier keeps working to detect bounce trackers, tracker collusion, and link decoration tracking.
Developer Guidance
If yours is among the few websites that still relies on third-party cookies in Safari and has not been affected by ITP in its previous iterations, here’s how you can make things work for your users:
Option 1: OAuth 2.0 Authorization with which the authenticating domain (in your case, the third-party that expects cookies) forwards an authorization token to your website which you consume and use to establish a first-party login session with a server-set Secure and HttpOnly cookie.
Option 2: The Storage Access API with which the third-party can request permission to get access to its first-party cookies.
Option 3: The temporary compatibility fix for popups, see section “Temporary Compatibility Fix: Automatic Storage Access for Popups” in our ITP 2.0 blog post. This compatibility fix allows the third-party to open a popup from your website and upon a tap or click in that popup gain temporary cookie access under the opener page on your website. Note that this compatibility fix will go away in a future version of Safari so only go this route if it saves you time and allows for a graceful transition period.
Cookie Blocking Latch Mode
The original release of ITP featured what we call “cookie blocking latch mode.” It means once a request is blocked from using cookies, all redirects of that request are also blocked from using cookies. Back in 2017 we got a request to allow cookie blocking to open and close on redirects and implemented that behavior. But with full third-party cookie blocking in place, latch mode is back.
7-Day Cap on All Script-Writeable Storage
Back in February 2019, we announced that ITP would cap the expiry of client-side cookies to seven days. That change curbed third-party scripts’ use of first-party cookies for the purposes of cross-site tracking.
However, as many anticipated, third-party scripts moved to other means of first-party storage such as LocalStorage. If you have a look at what’s stored in the first-party space on many websites today, it’s littered with data keyed as various forms of “tracker brand user ID.” To make matters worse, APIs like LocalStorage have no expiry function at all, i.e. websites cannot even ask browsers to put a limit on how long such storage should stay around.
Now ITP has aligned the remaining script-writable storage forms with the existing client-side cookie restriction, deleting all of a website’s script-writable storage after seven days of Safari use without user interaction on the site. These are the script-writable storage forms affected (excluding some legacy website data types):
- Indexed DB
- LocalStorage
- Media keys
- SessionStorage
- Service Worker registrations and cache
A Note On Web Applications Added to the Home Screen
As mentioned, the seven-day cap on script-writable storage is gated on “after seven days of Safari use without user interaction on the site.” That is the case in Safari. Web applications added to the home screen are not part of Safari and thus have their own counter of days of use. Their days of use will match actual use of the web application which resets the timer. We do not expect the first-party in such a web application to have its website data deleted.
If your web application does experience website data deletion, please let us know since we would consider it a serious bug. It is not the intention of Intelligent Tracking Prevention to delete website data for first parties in web applications.
Cross-Site document.referrer Downgraded to Origin
All cross-site document.referrers are downgraded to their origin. This matches the already downgraded cross-site referrer request headers.
Detection of Delayed Bounce Tracking
Some trackers have started to delay their navigational redirects, probably to evade ITP’s bounce tracking detection. This manifests as the webpage disappearing and reloading shortly after you land on it. We’ve added logic to cover such delayed bounce tracking and detect them just like instant bounces.
Testing Your Website
We encourage all developers to regularly test their websites with Safari Technology Preview (STP) and our betas of iOS, iPadOS, and macOS. Major changes to ITP and WebKit in general are included in the betas and STP, typically months before shipping. An easy way to stay ahead of the changes is to use STP as a daily development browser. This gives you access to the latest developer tools and helps you discover unexpected behavior in your websites with each release. If you come across bugs or breakage, please file an open source bug report.
Comments are closed.